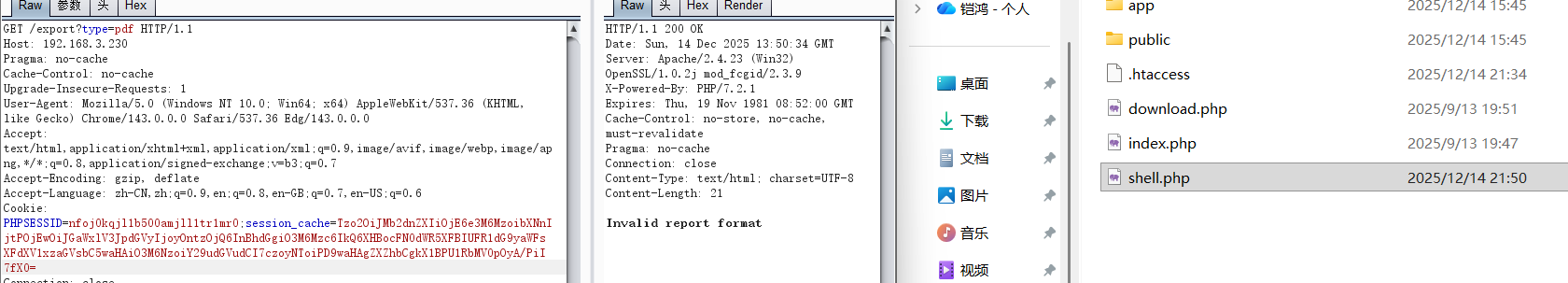
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
|
const express = require('express');
const cookieParser = require('cookie-parser');
const multer = require('multer');
const fs = require('fs');
const path = require('path');
const app = express();
const PORT = process.env.PORT || 3000;
app.use(express.urlencoded({ extended: false }));
app.use(cookieParser(process.env.COOKIE_SECRET || 'ctf_secret_where'));
const CACHE = {
users: {
}
};
app.set('view engine', 'ejs');
app.use(express.static('public'));
app.use(express.urlencoded({ extended: true }));
function waf(username) {
return String(username || '').replace(/[\{\}%()_]/g, '');
}
function getUsername(req) {
return req.signedCookies && req.signedCookies.username ? req.signedCookies.username : '';
}
function isLogin(req) {
return req.signedCookies && req.signedCookies.logged === '1';
}
const storage = multer.diskStorage({
destination: (req, file, cb) => {
const user = getUsername(req) || 'anonymous';
const dir = path.join(__dirname, 'media', user);
if (!fs.existsSync(dir)) fs.mkdirSync(dir, { recursive: true });
cb(null, dir);
},
filename: (req, file, cb) => {
cb(null, file.originalname);
}
});
const upload = multer({ storage });
const adminDir = path.join(__dirname, 'media', 'admin');
if (!fs.existsSync(adminDir)) fs.mkdirSync(adminDir, { recursive: true });
app.post('/admin', (req, res) => {
if (!isLogin(req) && getUsername(req) !== 'admin') {
return res.redirect('/');
}
const filepathRaw = String(req.body.filepath || '');
for (const bc of ['.','/', '*']) {
if (filepathRaw.includes(bc)) {
return res.send('no no no');
}
}
let filepath;
try {
filepath = decodeURIComponent(filepathRaw);
} catch (e) {
return res.status(400).send('bad encoding');
}
try {
const full = path.resolve(filepath);
if (!fs.existsSync(full) || !fs.statSync(full).isFile()) {
return res.status(404).send('file not found');
}
return res.download(full, path.basename(full));
} catch (e) {
return res.status(500).send('error');
}
});
app.get('/download', (req, res) => {
if (!isLogin(req)) return res.redirect('/login');
const user = getUsername(req);
const dir = path.join(__dirname, 'media', user);
let dirs = [];
try {
dirs = fs.existsSync(dir) ? fs.readdirSync(dir) : [];
} catch (e) {
dirs = [];
}
// render download.ejs with dirs
return res.render('download', { username: user, dirs, message: null });
});
app.post('/download', (req, res) => {
if (!isLogin(req)) return res.redirect('/login');
const user = getUsername(req);
const filename = String(req.body.filename || '').trim();
const userDir = path.join(__dirname, 'media', user);
// 读取用户目录文件列表(用于渲染页面)
const dirs = fs.existsSync(userDir) ? fs.readdirSync(userDir) : [];
// 空名处理
if (!filename) {
return res.render('download', { username: user, dirs, message: '请选择要下载的文件' });
}
try {
// 解析目标绝对路径
const target = path.resolve(userDir, filename);
const rel = path.relative(userDir, target);
const inUserDir = (rel === '' || (!rel.startsWith('..') && !path.isAbsolute(rel)));
const basename = path.basename(target).toLowerCase();
if (basename.includes('flag')) {
return res.render('download', { username: user, dirs, message: '该文件禁止下载' });
}
if (!inUserDir) {
return res.render('download', { username: user, dirs, message: '无法下载该文件(路径非法)' });
}
if (!fs.existsSync(target) || !fs.statSync(target).isFile()) {
return res.render('download', { username: user, dirs, message: '无法下载该文件' });
}
return res.download(target, path.basename(target));
} catch (err) {
console.error('download error:', err);
return res.render('download', { username: user, dirs, message: '下载失败(服务器错误)' });
}
});
app.get('/', (req, res) => res.redirect('/index'));
app.get('/index', (req, res) => {
const username = (!req.session || !req.session.username) ? 'visitor' : req.session.username;
return res.render('index', { username: getUsername(req), message: null });
});
app.get('/register', (req, res) => {
return res.render('register', { username: getUsername(req), message: null });
});
app.post('/register', (req, res) => {
let username = String(req.body.username || '');
let password = String(req.body.password || '');
username = waf(username);
if (username in CACHE.users) {
return res.render('register', { username: getUsername(req), message: '用户已存在 ' });
} else {
CACHE.users[username] = password;
const dir = path.join(__dirname, 'media', username);
if (!fs.existsSync(dir)) fs.mkdirSync(dir, { recursive: true });
return res.render('login', { username: getUsername(req), message: '注册成功,请登录' });
}
});
app.get('/login', (req, res) => {
return res.render('login', { username: getUsername(req), message: null });
});
app.post('/login', (req, res) => {
const username = String(req.body.username || '');
const password = String(req.body.password || '');
if (username in CACHE.users && CACHE.users[username] === password) {
res.cookie('username', username, { signed: true });
res.cookie('logged', '1', { signed: true });
return res.render('upload', { username: getUsername(req), message: '登录成功' });
} else {
return res.render('login', { username: getUsername(req), message: '用户名或密码错误' });
}
});
app.get('/logout', (req, res) => {
if (req.session) {
return req.session.destroy(err => {
try { res.clearCookie('connect.sid'); } catch(e) {}
try { res.clearCookie('username'); } catch(e) {}
try { res.clearCookie('logged'); } catch(e) {}
return res.redirect('/');
});
}
try { res.clearCookie('username'); } catch (e) {}
try { res.clearCookie('logged'); } catch (e) {}
return res.redirect('/');
});
app.get('/upload', (req, res) => {
if (!isLogin(req)) return res.redirect('/login');
return res.render('upload', { username: getUsername(req), message: null });
});
app.post('/upload', upload.single('file'), (req, res) => {
if (!isLogin(req)) return res.redirect('/login');
if (req.file) {
return res.render('upload', { username: getUsername(req), message: '文件上传成功' });
} else {
return res.render('upload', { username: getUsername(req), message: '上传失败' });
}
try {
// multer 已保存文件
return res.json({ code: 200 });
} catch (e) {
return res.json({ code: 500 });
}
});
app.use((req, res) => {
res.status(404).render('index', { username: getUsername(req), message: '页面不存在' });
});
app.listen(PORT, '0.0.0.0', () => {
console.log(`Server running at http://localhost:${PORT}`);
});
|