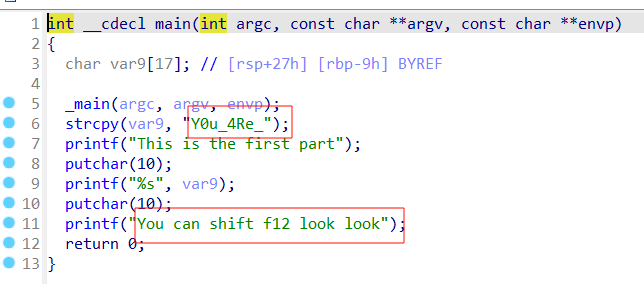
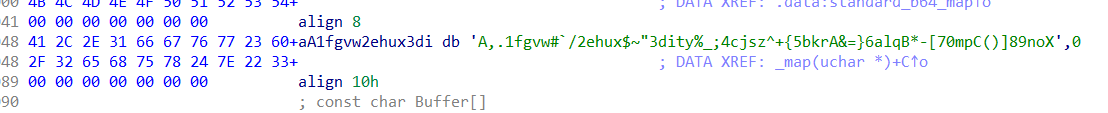
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
|
import numpy as np
from scipy.optimize import lsq_linear
# Manually extracted coefficients for each equation (16 equations, 20 variables)
# Each row corresponds to an equation, each column to byte_14000A668[1] ... byte_14000A668[20]
A = np.array([
[283, 860, 616, 575, 891, 758, 851, 773, 931, 323, 257, 141, 987, 965, 908, 417, 978, 410, 887, 948],
[148, 421, 151, 111, 80, 580, 62, 974, 954, 589, 718, 938, 708, 35, 68, 568, 50, 920, 490, 938],
[182, 506, 674, 948, 113, 11, 392, 409, 892, 932, 920, 95, 622, 778, 335, 489, 222, 668, 590, 908],
[707, 571, 180, 716, 570, 890, 427, 447, 728, 465, 479, 34, 624, 773, 266, 891, 399, 410, 859, 479],
[807, 771, 199, 437, 169, 873, 49, 282, 814, 459, 679, 142, 304, 949, 901, 71, 716, 380, 798, 556],
[83, 496, 231, 469, 385, 235, 654, 522, 917, 369, 35, 25, 322, 856, 831, 156, 198, 979, 898, 465],
[585, 194, 33, 220, 376, 787, 648, 50, 195, 711, 747, 688, 236, 758, 708, 787, 793, 260, 928, 305],
[859, 273, 803, 976, 7, 443, 541, 653, 701, 311, 964, 848, 0, 136, 588, 598, 909, 22, 573, 767],
[95, 883, 236, 81, 818, 634, 181, 365, 215, 9, 799, 456, 768, 377, 744, 397, 164, 507, 59, 776],
[789, 422, 942, 606, 792, 806, 905, 484, 773, 998, 300, 933, 240, 617, 689, 960, 423, 381, 234, 873],
[988, 898, 212, 175, 845, 114, 828, 414, 603, 817, 736, 590, 696, 343, 305, 211, 900, 283, 7, 766],
[961, 466, 70, 860, 886, 729, 689, 998, 689, 735, 996, 121, 952, 366, 501, 574, 106, 788, 30, 220],
[866, 701, 620, 141, 540, 907, 604, 271, 299, 136, 79, 316, 49, 283, 362, 156, 864, 522, 748, 313],
[913, 999, 674, 979, 147, 646, 701, 749, 991, 110, 406, 144, 770, 438, 224, 159, 26, 425, 399, 922],
[164, 725, 0, 454, 269, 784, 41, 797, 439, 325, 74, 779, 743, 654, 484, 153, 421, 225, 537, 13],
[220, 200, 789, 41, 562, 404, 683, 818, 978, 82, 634, 436, 176, 433, 42, 485, 204, 874, 210, 591],
[915, 721, 268, 410, 715, 587, 491, 409, 822, 848, 899, 124, 240, 820, 858, 902, 532, 928, 597, 584],
[875, 934, 726, 149, 287, 901, 477, 623, 560, 633, 53, 411, 28, 623, 160, 512, 180, 327, 302, 421],
[133, 587, 834, 291, 780, 367, 69, 17, 934, 666, 495, 295, 15, 980, 170, 462, 649, 792, 434, 838],
[391, 316, 66, 495, 554, 894, 745, 300, 684, 42, 69, 620, 179, 233, 854, 475, 224, 420, 422, 41]
])
# Right-hand side vector
B = np.array([
913686,
630335,
707525,
724203,
688899,
604784,
665485,
727664,
572015,
875498,
714759,
778853,
584591,
717586,
537823,
587367,
842245,
610801,
653127,
533470
])
# Define bounds for the byte values (0 to 255)
bounds = (0, 255)
# Solve the system using bounded least squares
# We expect an exact solution, so check for residuals near zero.
result = lsq_linear(A, B, bounds=bounds)
# Check the result
if result.success:
solution = result.x
# Check if the solution is close to integers and within bounds
if np.allclose(solution, np.round(solution), atol=1e-5) and np.all((solution >= 0) & (solution <= 255)):
flag_bytes = np.round(solution).astype(int)
# Verify the solution by plugging back into the equations
if np.allclose(np.dot(A, flag_bytes), B, atol=1e-5):
print("Found integer solution:")
print(flag_bytes)
# Convert bytes to ASCII characters
flag = "".join([chr(b) for b in flag_bytes])
print("Decoded Flag:", flag)
else:
print("Found bounded solution, but it does not satisfy the equations exactly.")
print("Solution:", solution)
else:
print("Found bounded solution, but it is not an integer solution within bounds.")
print("Solution:", solution)
else:
print("Optimization failed:", result.message)
|