web
直接dirsearch扫描得flag.php即可
预期解打Laravel v11.x PHP反序列化漏洞分析(CVE-2024-40075)
|
|
Laravel v11.x PHP反序列化漏洞分析(CVE-2024-40075)-先知社区
misc
three-ucsc
盲水印命令
|
|

得到8f02d3e7
然后二进制转base64转摩斯

-ce89-4d6b-830e-
流量包追逐流一翻找到part3密码

得到5d0cb5695077
最终flag{8f02d3e7-ce89-4d6b-830e-5d0cb5695077}
小套不是套
第一个二维码一扫得到tess的密码!@#QWE123987。
第二层是个伪加密,09改00

得到图片

补充残缺的png头+Our Secret解密
010打开,FFD9其实是给确少png文件头的png。为什么?首先png文件头格式是
|
|
且一定有IHDR数据块

然后0D 0A 1A 0A开始复制到png文件尾(IEND块00 00 00 00 49 45 4E 44 AE 42 60 82)

在这段数据块前添加png文件头89 50 4E 47就组成了一个新的图片

但是其实不对,后面的数据块也要加上,因为这个特征是oursecret隐写
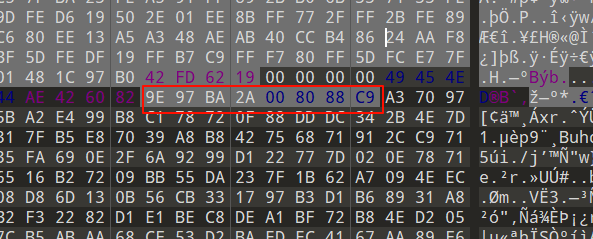
后面其实这就是隐藏的数据,所以用Our Secret来解密(文档隐藏,解密工具)

crc爆破
但是Our Secret解密需要密钥,所以肯定来自于套.zip,看里面全是很小字节的文件,再看看crc,那肯定是crc爆破(爆破每一个压缩包的CRC值获取有意义的字符串)

网上没有什么按顺序自动化的提取压缩包crc并爆破crc得到结果,下面这个可以很快的提取crc,但是爆破很慢,而且不能将爆破后的crc结果按顺序拼接在一起,不过可以用它提取出crc,然后我们写脚本爆破!
工具GitHub - AabyssZG/CRC32-Tools: Easy CRC32 Tools,so easy!!!
CTF-Misc Guide - ⚡Lunatic BLOG⚡
|
|

很快就提取出来了,然后让ai将这些crc按文件顺序排序,再爆破,再拼接就好了。(其实将这堆数据给ai,让它排序,它就自动排序了)
|
|


再随波逐流梭哈一下得到Key is SecretIsY0u,所以密钥就是SecretIsY0u
|
|

当然这里偷了一个大佬的脚本
|
|
运行python crc32.py即可,这个更慢,但是没什么字节限制
爆破之后就是解密了

这题套题有点难受:伪加密+补全残缺png+crc爆破+our Secret解密
USB
CTF中我的USB键盘鼠标流量解密指南和脚本 - FreeBuf网络安全行业门户
USB - 流量分析 - 流量 | nnnpc’s Blog = 低头学习 抬头看路 = 很多人已经做到了,而他们都曾经和现在的你站在同样的起点上
先去kali执行命令提取数据
|
|
然后写代码解密即可
本来想用上面文章的工具,但是脚本还需要根据实际情况修改,所以索性直接gpt写脚本处理提取出来的data.txt
|
|
当然上面的3篇文章也讲述了鼠标流量。这里代码参考UCSCCTF2025 - Misc - WriteUp|2hi5hu-研习足迹
No.shArk
先把所有可疑文件全部dump出来


经过分析,发现可疑文件cat.png(010打开发现key)
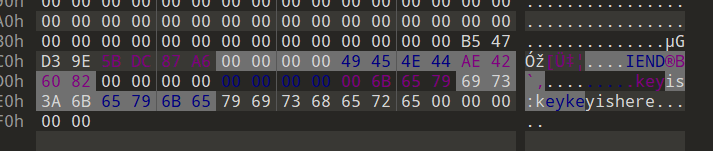
png末尾有keyis:keykeyishere,不知道啥用先放这
dns协议隐写
这时候发现有些流量包含有大量01数据,显然很可疑

根据流量地址用tshark导出
|
|
去除无用数据,放到010文本编辑器

乍一看不就是二维码嘛,直接写代码转换为二维码(由于这个数据有25行,51列,所以横向2字符一像素)
|
|

但是少了2个定位符,直接上ps,将左上的定位符ps上去

微信扫码得到Y0U_Fi8d_ItHa@aaHH(微信识别二维码功能很强,我ps技术不好很多二维码识别工具都不好识别,但是微信可以)
snow隐写
然后发现w1.html也很可疑,发现其数据里有大量制表符。

刚好符合snow隐写
然后snow解密得到一半flag。但是前面的key试了不对,所以试这个二维码扫出的值,
|
|

11ef-b3b6-a4b1c1c5a2d2}
jpg silenteye隐写
但是我们从FTP-DATA导出来一jpg,还一个密钥没用,所以这里想到考关于jpg隐写,尝试一番想到silenteye,密码是前面的key,得到3个字符与其值

shuffle=5,a=7,b=3
Arnold猫脸变换
这里由这些参数和cat.png与宽高大小相等可以想到猫脸变换(变换后图像变成了像白噪声一样无意义的图像,符合图像。并且其只要确定shuffle,a,b这三个参数即可还原图片)
|
|

当然其实什么参数不知道也行,直接爆破参数
|
|
考的很多,dns隐写+snow隐写+silenteye隐写+猫脸变换,甚至还考一点二维码,很难了
参考:
2025 UCSCCTF Misc Writeup - ⚡Lunatic BLOG⚡
UCSCCTF2025 - Misc - WriteUp|2hi5hu-研习足迹